I sure don’t feel safe just ignoring it, considering the frequency.
deleted by creator
The message is multi-factor
Oh, I missed that in the gutter of the message.
This is a common attack tactic, then, called MFA Fatigue. It also means they probably have Ops password already. Or Ops service provider is doing something dumb. (MFA requests shouldn’t be sent out without the other factor being known.)Edit: There’s no approve link there. Just ignore these. If you got a lot of these, do setup MFA.
It’s not mfa fatigue. MS sends a code to the email. There is no accept or deny in the email.
Oh. Yep. That says “Archive”. I gotta stop reading here when I’m tired.
deleted by creator
It’s common for people to get these when their email address is similar to my dad’s and he forgets his password again.
Part of my concern is the email has part of an uncommon spelling of name + some numbers. And that it started all of a sudden, every day. The email is several years old and only now it’s begun happening every day.
I hope you’ve turned on 2FA.
FYI, the emails the OP are getting are the 2FA Time-based One-Time Password (TOTP). So OP in fact does have 2FA enabled. 😊Ps. I’m not being sarcastic.Never mind. I misunderstood what the email was being sent for. My apologies.
Create an email alias and use it as the account address.
Have you been pwned?
There’s been some new and ginormous data dumps recently.
Maybe it is your time.
Change your password immediately to something you’ve never used before and isn’t similar to current passwords. If you’re getting random 2fa codes, someone is able to complete your first factor, so fix that ASAP.
It might not be 2-factor. Microsoft has an option to log in via email code, which doesn’t need a password.
I had the same issue as OP, spoke to Microsoft who said I didn’t need to change my password. I think these are sent before the password is confirmed.
deleted by creator
It is actually safe to ignore them. It means either someone has an email address similar to yours, or a bot of some sort has you email address and only your email address.
Essentially, someone or something goes to the login screen, enters your login, and says “I don’t have the password, let me in!”.
Sending a code to your email like this is the first step in letting someone in without the password, or more specifically to having them reset it.Since the email is to check “did you ask for this?”, doing nothing tells them that you did not.
If you want some extra peace of mind: https://account.live.com/Activity should show you any recent login activity which you can use to confirm that no one has gotten in.
Also, use two factor, a password manager, and keep your recovery codes somewhere safe. The usual security person mantra. :)
This is all good information and seems well intentioned, but it’s worth pointing out in a post about account security that clicking links provided by others and giving it your login information is very unwise (even/especially links in emails like these). For the link you provided, it’d be better to recommend going through a primary microsoft page or login that can be confirmed by the user and getting to the activity history page from there
That is wonderful advice and I’m glad you pointed that out. :)
If I knew how to give directions to the page, I would, but unfortunately I don’t know the Microsoft site layout, only the URL that their help center directed to.
In mitigation of my indiscretion: it’s generally safer to trust a person you approach out of nowhere than to trust someone who approaches you out of nowhere.
Since they chose the venue and asked the question, the likelihood that an attacker is present in the replies is lower than the expectation that an unsolicited email is from an attacker.But it’s also entirely correct to be distrustful of anything anyone asks you to click on, triply so if it involves security or login pages.
For MS guides there usually is an article under support.microsoft.com or learn.microsoft.com (usually more advanced, admin related documentation for company / enterprise level stuff) domains. Here’s an article for checking activity.
Also, use two factor, a password manager, and keep your recovery codes somewhere safe. The usual security person mantr
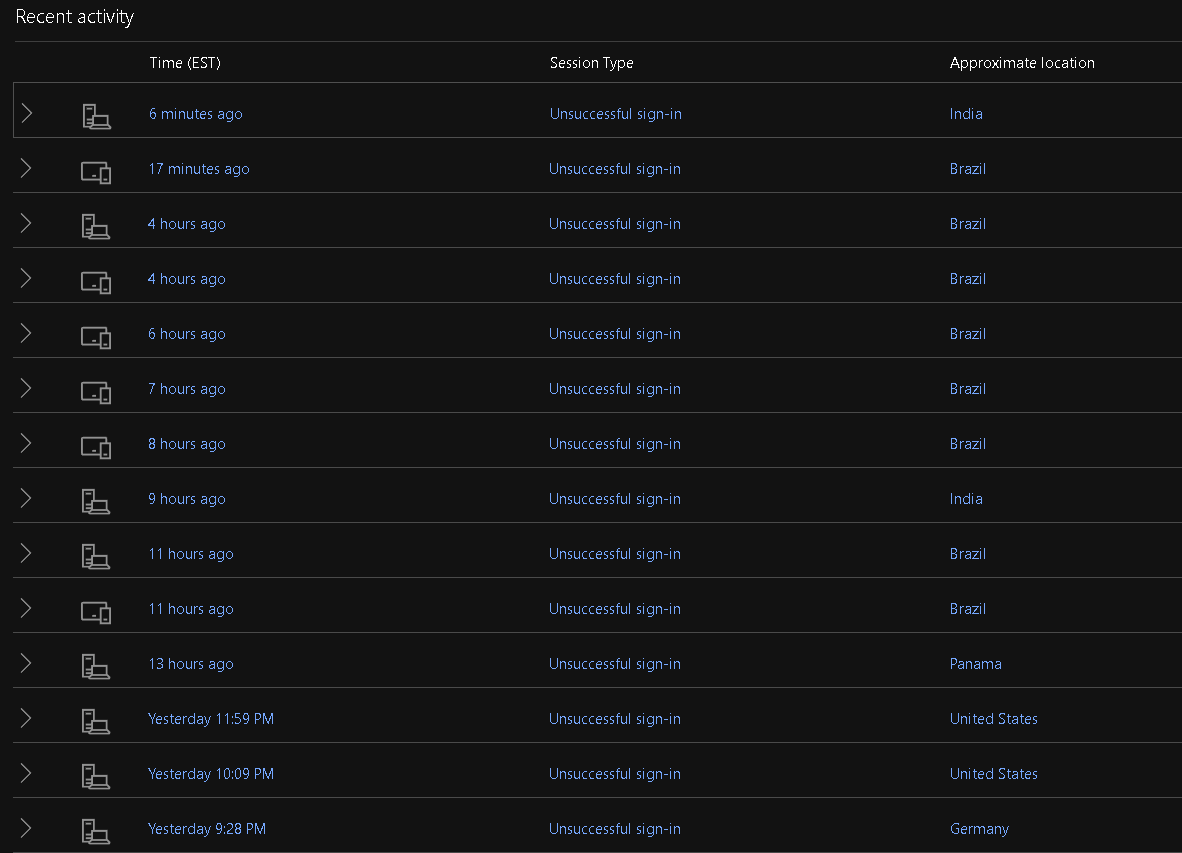
Well, I found the recent activity and none of these were me. At least they all appear to say Unsuccessful sign-in.
deleted by creator
FWIW Microsoft does a blind token here meaning they send it if your password is correct or not.
In that way the person attempting to gain access has no context of if the password is correct or not
deleted by creator
It’s just login attempt when you’re setup this way.
It happened to my account AFTER I changed the password.
I do not believe accounts are setup this why by default and Microsoft does encourage you to use better 2fa as well.
Requiring a token + password before authentication is attempted is common, the password being entered triggers the token but it doesn’t mean you’re in.
This is not Microsoft doing something wrong, it’s Microsoft protecting an account that ought to have been protected better.
OP needs to go in and configure actual 2factor
In the same way google will log the location and browser fingerprint and whatnot from attempted logins whether they’re successful or not.
Yup, that would indicate that likely a bot is trying to guess it’s way in.
You are still safe.
The only weird thing here is that Microsoft lets such things bother you instead of guessing that you didn’t teleport to Brazil and instead putting a little extra burden on the Brazil end before sending you an email.
If you’re still feeling worried, the biggest thing you can do is enable two-factor auth (which you should do anyway), or even better: enable something like passkeys which are very secure and also easier than username/password.
Two-factor/password manager is the “remember to brush and floss” of the security industry, so… Please do those things. :)
Considering most of the attempts are from India and Brazil I suspect a service you signed up for has sold your email to unsavory data brokers and now a bunch of scam companies are doing that MFA attack on you
You can create an email alias for your Microsoft account and then only enable login from that account. If you then do not use that email for anything but the login, you should be pretty safe from credential stuffing attacks.
I had a very similar issue with multiple failed login attempts and changing my login email stopped it right away.
I would definitely changw your password, also see if you can check the logs of login as it will sometimes show and you can see if the country aligns.
For what its worth, if you think youre not being hacked. It sometimes ive seen it come up when people use a vpn and are connected by some sort of app. And it flags a 2fa to reconect. Its unlikely but i have seen it.
If this isn’t a phishing email itself, your email address was probably harvested from a compromised site you used it to sign up with. There are sites where you can check to see if it’s compromised. This is why I started using email aliases when signing up for any site or service. It shows where it was compromised or you’ll find some companies will share it with partners or sell your info sometimes.
When you say email aliases, what do you mean? A lot of services strip plusses from emails now, right?
You can use something like SimpleLogin to create email aliases that can’t be traced back to your real email address.
Edit: other options are available, such as Firefox Relay which does exactly the same thing.
I used to use Relay but they had gotten added to a couple of disposable email block lists and because of that started having issues with my accounts…
Idk if SimpleLogin has that same issue or if there’s a way around the problem entirely
Thank you, this is really helpful!
Not sure. But Proton, Apple,
passmailSimpleLogin (got names mixed up) and some other providers have a way you can create email aliases on the fly that forward to your real address. I think Microsoft does too but it was limited last time I looked at it.Thank you, I’ll look into options.
Use Microsoft authenticator on your account, it won’t stop people from trying to access your account but you’ll stop getting these and it’s generally safer than any kind of email based 2fa
Change your password to a randomly generated password and them setup 2FA
Do not click on anything in the emails as they may be phishing attempts
Just to be clear, change your password by manually typing in the address of the service in question.
Do not use the link in the email to navigate to the service for password changing.
I got one of these emails. It isn’t even MFA, nothing to reply with the code to. It doesn’t even say which Microsoft account, it sent it to my GMail recovery account. It’s so utterly bad not being able to trace the attempt to its source. It’s sus that I’m not the only one to have recently experienced this out of nowhere. Maybe it’s an attempt to farm valid Microsoft emails from the way this service behaves?
If it happened on a MS account you have, you can check the activity part of the account, it should list all login attempts and give you an IP for each.
What email address did it come from, no links in it at all? I would assume phishing attempts that would be coming from a BS email that has a link to either go sign in or change your password which would send you to a site and then collect your entry, thereby gathering your actual sign in info.
That can be compiled into other data over time and eventually whoever purchases or collects it all with have a full set, or immediately have a full set when they try those credentials on other sites that may not have 2 factor set up.
I started getting these after the lastpass hack.
When I started getting those I closed my account down, just to be sure. I don’t even remember why I had a MS account.
I don’t even remember why I had a MS account.
If you’re of a certain age, probably MSN Messenger
I am of a certain age and I did use MSN Messenger back then, but I find it unlikely - it’s calling me by a pseudonym that I coined rather recently. (There’s no way I give my actual name to businesses out there, unless I’m planning to buy stuff.)
Do you have 2 factor authentication set to be sent to email? If not, it is definitely phishing but unfortunately they might be able to spoof an official microsoft email account.
Is the “Microsoft account team” email coming from an official email account? If not, it is definitely phishing and you can block the address and report as spam/phishing.
I get em too fam. Sure up your passwords (I use bitwarden) and 2fa everything and you’ll be fine. I’ve ignored them for years and all is well.
I’ve gotten a bazillion of these in the past couple years. According to Microsoft I can safely ignore it so I guess I’ll just do that since I’m not sure what else to do about it.
I have the same issue. I used the email when I was in Nigeria for work, so I figured it came from that, but now I’m not so sure.











