I was willing to overlook:
-
The bed costs $2,000
-
It won’t function if the internet goes down
-
Basic features are behind an additional $19/mo subscription
-
The bed’s only controls are via mobile app
You have to be crazy to pay for a product like this. You don’t need to be a security researcher to make an educated guess that the company behind this “bed” is going to spy on you.
Eight Sleep is clearly onto something, having raised $110 million dollars in venture capital, exceeding $300 million dollars in annual revenue.
I would have never thought this Eight Sleep outfit had hundreds of millions of dollars in revenue.
I just looked at their Privacy Policy/ToS.
EDIT: Accidentally hit post.
Anyway, based on their terms, the customer data is definitely the actual product. In addition, the wording makes it seem likely that the de-identification is pretty weak.


Further details that should give anyone pause.
Admitting to not respecting “Do Not Track” signals, because they are not legally required to:

Mention of collecting data about gender at birth, whether one regularly sleeps with a partner, and menstrual cycle regularity:

These guys are creepy as fuck, without even getting to the possible backdoor. They are selling customer data with a contractual pinky-swear to not re-identify the data (this being mentioned, to me, means that there is a plausible means to do so). So.
What kind of creepiness could this data be used for?
-
Potential for blackmail/kompromat. (using sensors to detect patterns of sexual activity that could be infidelity or “sexual deviancy”)
-
Targeting people who may have had abortions.
-
Signs of not following religious doctrine (premarital sex, sex for purpose other than procreation, etc)
-
Checking whether the person is home and likely sleeping.
-
Spying on employees during their off-work hours (not that it’s ok during work hours) and/or scrutinizing sick leave.
There are a lot more possibilities. Way too dystopian and creepy.
Trash company with a trash CEO. Until we start treating digital privacy on the same level as physical privacy, this sort of stuff will continue.
Sounds like they’re from Texas.
Edit: Nope. New York somehow.
-
Ultimately I lost this argument and I will say their pad is better designed than their competition. I love the concept of pairing that pad which is good and harmless by itself with a different temperature controller. I kind of hoped for an alternate firmware for this device, since the hardware of the temperature controller is also well done apart from lack of buttons/remote controller.
That’s fair. I guess for me personally a “smart” bed that’s also tied to mandatory subscription is an outlandish concept.
Yeah, it was rough for me since I advocated for other options that weren’t this way, but had to admit that the engineering on the eight sleep just got to a better physical experience.
FreeSleep looks promising. Currently grandfathered into the pre-subscription required reality, but fully expect that to evaporate and then it’s off to do the FreeSleep stuff. I anticipate a local control loop will be so much better, and maybe be able to create tactile controls in a wifi based remote control.
-
Does that mean if your laptop is on your network, they can control and access that?
Beyond the basics, what does access to a device on your home network grant them? Any other device connected to that home network - smart fridges, smart stoves, smart washing machines, laptops - is typically routable via your bed. The (in)security of those devices is now entrusted to random Eight Sleep engineers.
It means that they can effectively use it as a VPN to access your private network, if like most, it is on the same network as other devices.
Really though, that’s of little concern compared to their sale of sensitive customer data
can effectively use it as a VPN to access your private network
I’m dumb. I still don’t know what that means. When they can access your network, does that mean they can make copies from your printer or does that mean they can access your hard drives?
If you have your HDD shared with local network devices without a password, then yes they can access those HDDs. Not sure about printers, but if the printer is not locked down some how, they can potentially access it (e.g. print or scan documents that are in the scanner), albeit I haven’t used a printer at home in decades so I may be wrong.
It’s not a good thing to have randoms (even a nominally legit company) to have open 24/7 access to your local network.
Thank you for the explanation, so it’s as bad as I thought. How do I know what apps and programs have access to my network?
It’s more devices that enable apps and programs to have access to your local network.
There are no easy and fast solutions. The best option is to avoid all “corporate” (i.e. non-DIY) smart devices and never connect them to the internet. It may be helpful to get a Pi-Hole running which provides a final layer of defence that catches and block’s random stuff (but not everything).
Pi-hole is also a fun project for getting into SBCs/Raspberry Pi. It’s cheap and you get a nice little dashboard of all the spyware that it blocks:
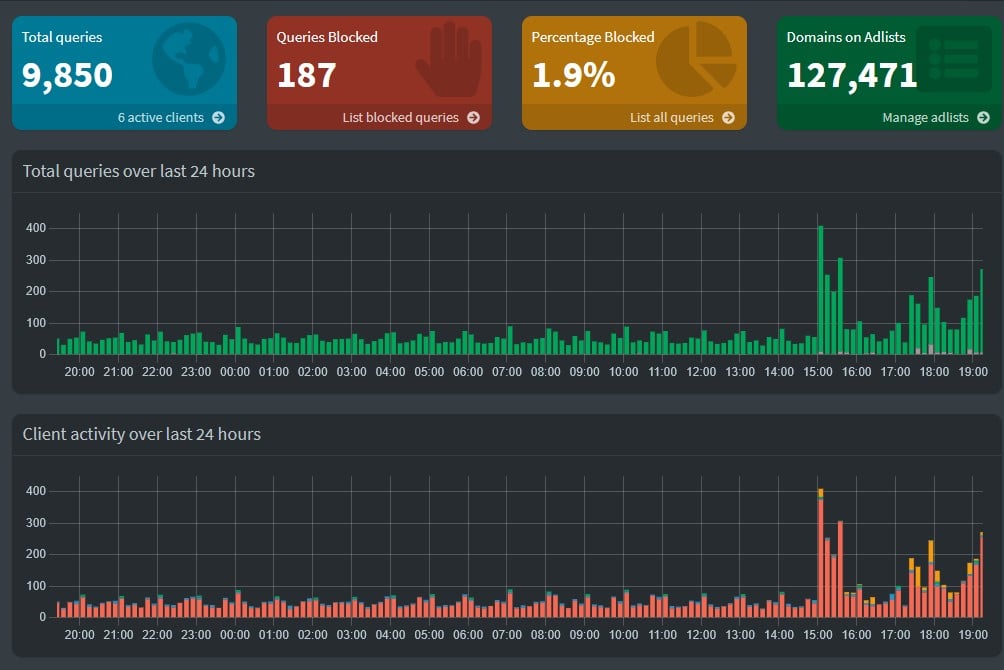
I will note that a Pi-Hole most probably won’t help against Eight Sleep (since it sounds like you need it to have remote access to use it), but it’s good to block random spyware embedded in many seemingly legit applications.
You can also add a bunch of useful services to the SBC/Raspberry Pi like NAS, Media Server, download client and much more.
Got you, I’m screwed because I have a smart tv. I didn’t realize that they could all talk to each other. I didn’t care if they saw what I watched, I do care if they can get on my laptop or phone.
They might not necessarily get on your laptop or phone (to be honest they probably can’t), but there is a risk they can.
I would strongly recommend using the TV purely as a HDMI output device and not using the “smart” functions of the TV. Buy yourself a Raspberry Pi (it will cost less than $100 out of pocket even if you go overboard) and set up a media server with say Kodi or Jellyfin. PM me if you feel like it and I will point you in the right direction (good forums where people will help you and answer intro questions without being annoying).
youd need a proper firewall to actually know for sure, or set up some sort of network sniffing.
a simple countermeasure is isolating clients between themselves when applicable, even most consumer grade routers can do it.
this may or may not break functionality, but if the app stops working without internet, chances are its going to the internet instead anyway and its gonna be fine.
I’m dumb.
Please do not insult yourself. Not having knowledge in a technical discipline does not mean anything about your intelligence.
So, I think that that OP explained pretty well but, I will try to provide some additional info and context, because I’m a neurospicy Linux nerd who has worked with Linux-based tech for over a decade:
There are a couple of terms and topics that need to be explained for this to make sense:
- Private vs Public network (and common home networks)
- Virtual Private Network (VPN)
- Secure SHell (SSH)
First, public vs private networks. I’m not going to do a full CCNA course but a high-level here. I’m going to simplify while trying to remain accurate.
What is a network? A group of devices (PCs, printers, phones, etc.) that can all talk to each other, without needing a router to connect them. Generally, everything goes through a device called a switch.
What is a router? A device that connects two or more networks.
What is a switch? A device that passes traffic between devices on a network.
What is a public network? Effectively, this is interchangeable with “the Internet”. Every server and device that is directly connected to the Internet has an IP address.
What is a private network then? It is a network in which only local devices are able to connect. The IPv4 addresses will generally be 192.168.x.x or 10.x.x.x (172.16-18.x.x is also reserved for this purpose). These addresses are special in that they are, by the IP protocol specification reserved for this purpose and not allowed for use or routing on the Internet.
How does this relate to home networks? First of all, most common home networks use a “gateway” device that is a combination of a router, switch, and wireless access point. This device generally is dynamically assigned a public IP address by the ISP and handles routing traffic between the private network of customer devices and devices on the Internet. This is, intentionally, one way (private network -> public network), both to improve customer security and to allow upcharging those that wish to self-host their own websites, etc.
Generally, all local traffic is on one private network (occasionally with a separate “guest” network). What this means is that any device on the home network is able to talk to any other device on it.
TL;DR #1 - Private network is your home network. Public network is the Internet.
What is a VPN? First, let me say what it is NOT, because there is a lot of misinformation and disinformation on the topic. A VPN is NOT a privacy/anonymization tool. A Virtual Private Network is simply a way to securely connect two or more private networks, using public network endpoints. The traffic routes through pubic network nodes, just like any other traffic, but is encrypted, so that the data is not readily known but, the origin and destination are basically plain text.
TL;DR #2 - VPNs connect two or more private networks, using encryption over the Internet.
What is SSH? Secure SHell is a protocol that allows one to securely connect to a Linux or other unix-like device for command-line access. Frequently, a piece of SSH functionality called reverse tunnels is used by tech companies to remotely support Linux-based appliances. This effectively provides the same functionality as a VPN but with access specifically to the Linux host.
How does this relate to backdoor, etc? This means that the smart bed company can log into the Linux computer in the bed and do anything that a device on the customer’s private network is allowed to do.
This could include things like:
-
Logging into any device (PC, printer, smart oven, etc) that has default or weak credentials.
-
Causing network congestion.
-
Compromising the customer’s gateway device to act as a Man-in-the-Middle to spy on network traffic.
-
Pulling known illegal content from the Internet to act as incriminating evidence against a political dissident to justify their arrest.
Holy shit dude, this explains so much. Thank you for taking the time to type that all out.
You’re very welcome! I’m glad that I could help make it a bit easier to understand :D
What the article is saying is that they can use the bed as a back door into your home network. From there they operate at the same trust level as anything else on your local network, and anything on your lpcal network that would be vulnerable to an attacker on your local network would be vulnerable to them.
How do they bypass the NAT to route ssh traffic to the bed? Does the bed have a built in phone home VPN connection to enable this?






